# Audit Log with S3
# Preamble
This guide explains how to instruct Psono to send audit logs directly to S3. We assume that you have followed this general
guide for audit log to configure the audit logs and see now events in your
audit.log file.
TIP
This feature is only available in the Enterprise Edition.
# Shipping Logs
To ship your logs you need to create an S3 bucket, some credentials for that S3 bucket and configure then Psono to use these credentials.
# Create bucket
Login to aws.amazon.com
Go to S3
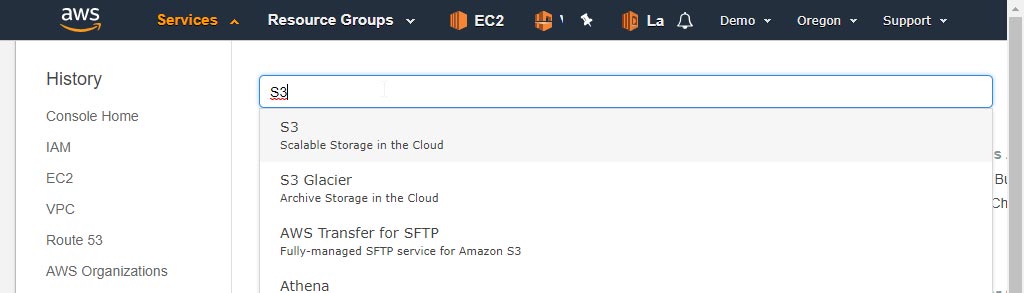
Click "Create bucket"
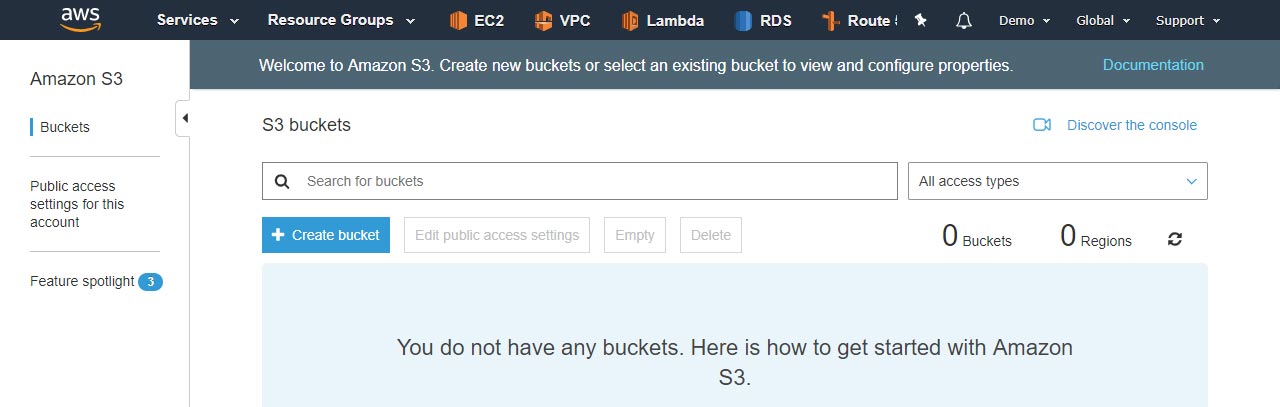
Specify bucket information and click "Create"
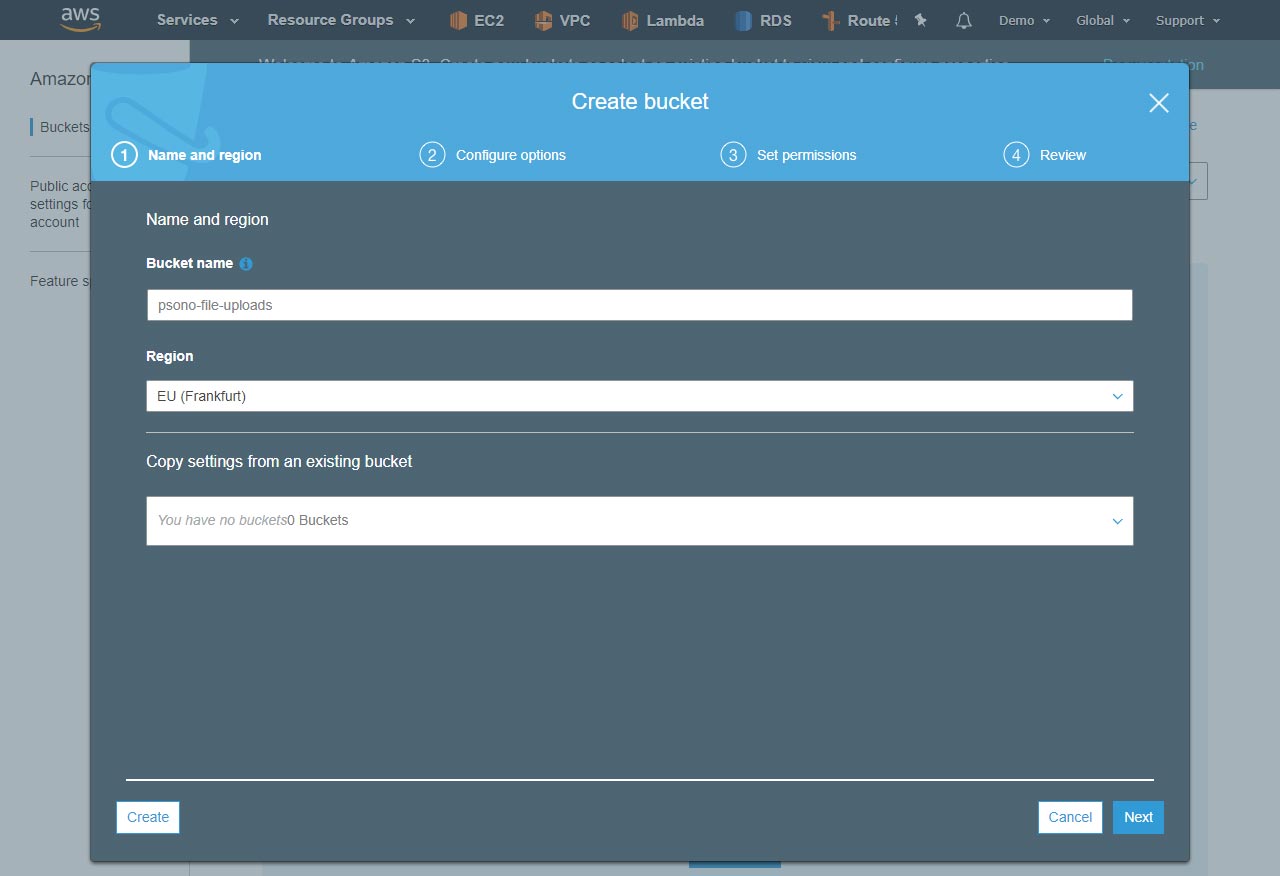
TIP
Remember the bucket name. You will need it later.
# Create a policy
Go to IAM
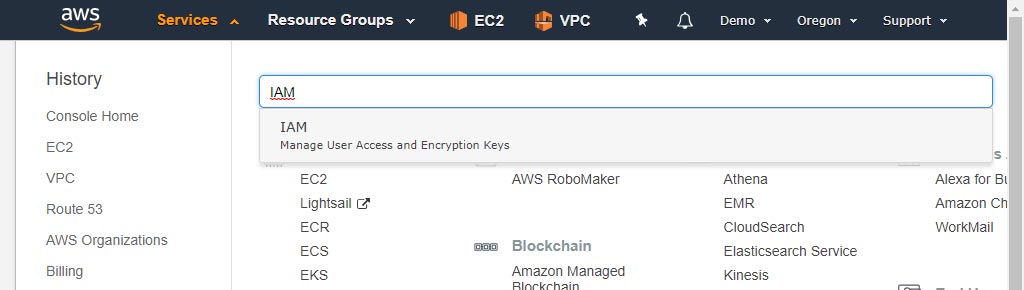
Go to Policies and click "Create Policy"
Select JSON
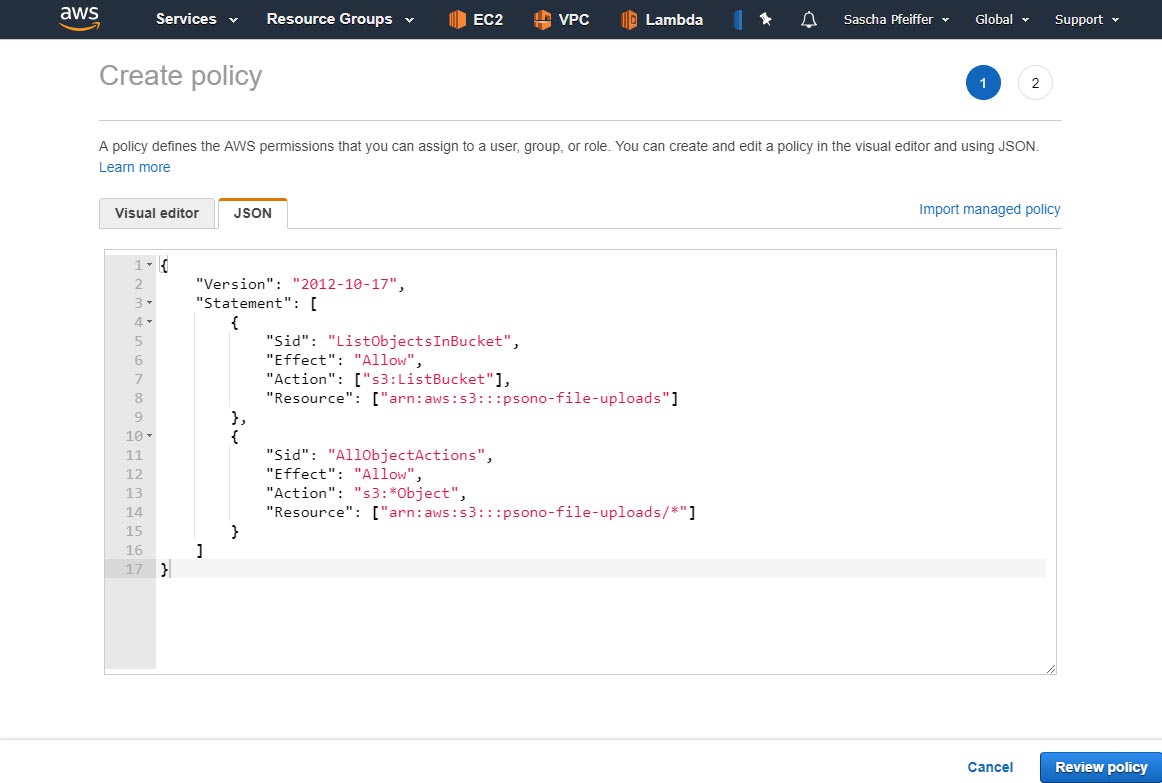
and paste the following config:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "ListObjectsInBucket", "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::psono-file-uploads" ] }, { "Sid": "AllObjectActions", "Effect": "Allow", "Action": "s3:*Object", "Resource": [ "arn:aws:s3:::psono-file-uploads/*" ] } ] }
TIP
Replace psono-file-uploads with your bucket name
Click "Review Policy"
Specify a name and description
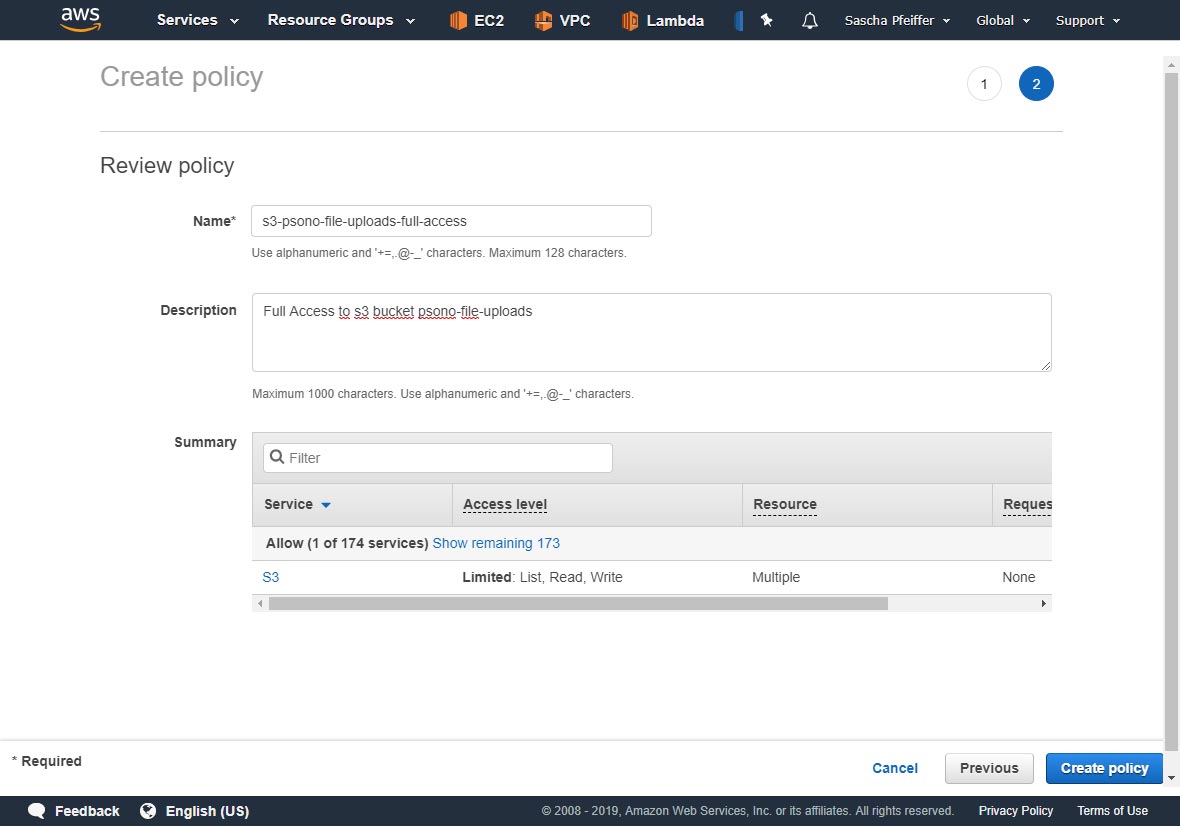
Click "Create Policy"
# Create a user
Go to IAM

Go to users and click "Add User"
Specify a "name" and allow "programmatic access"
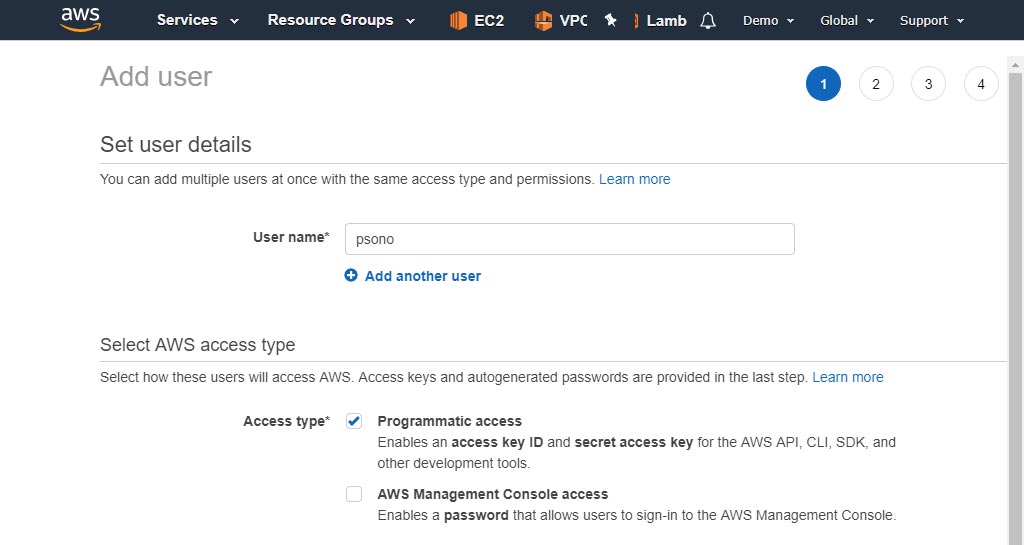
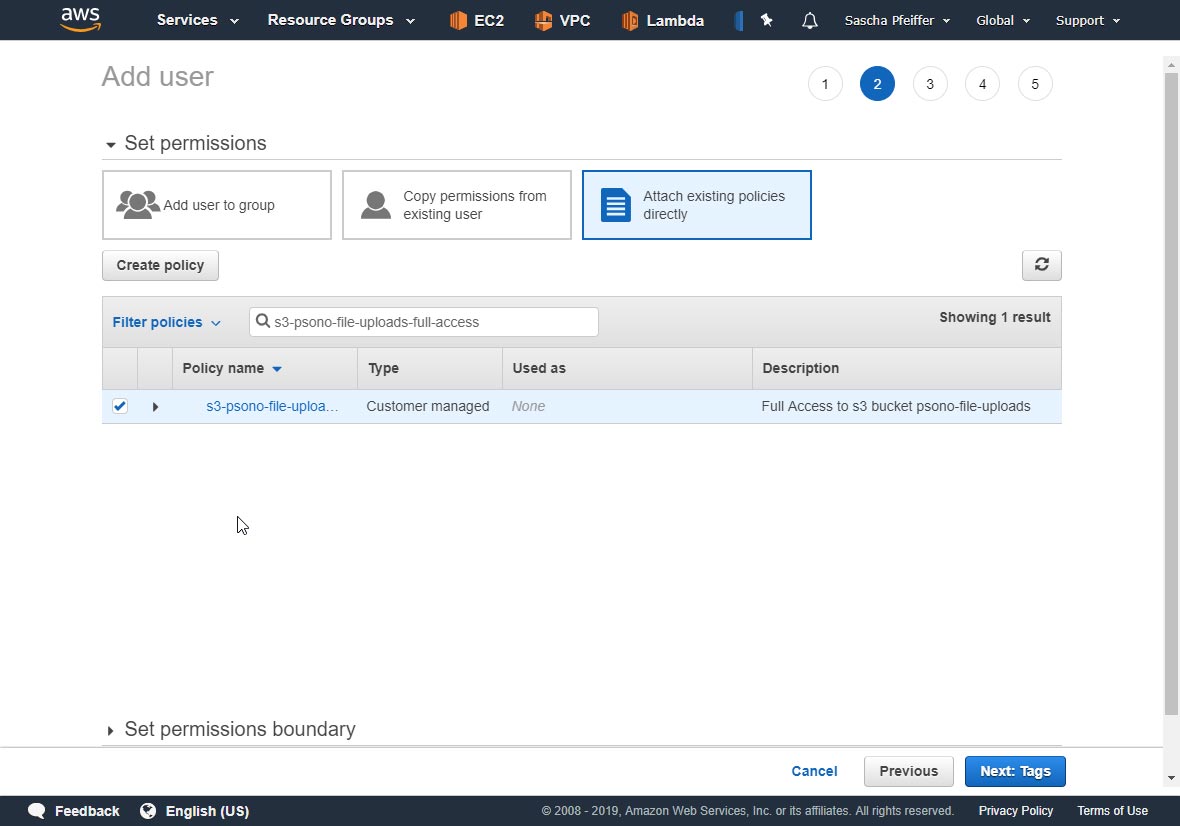
Attach your policy
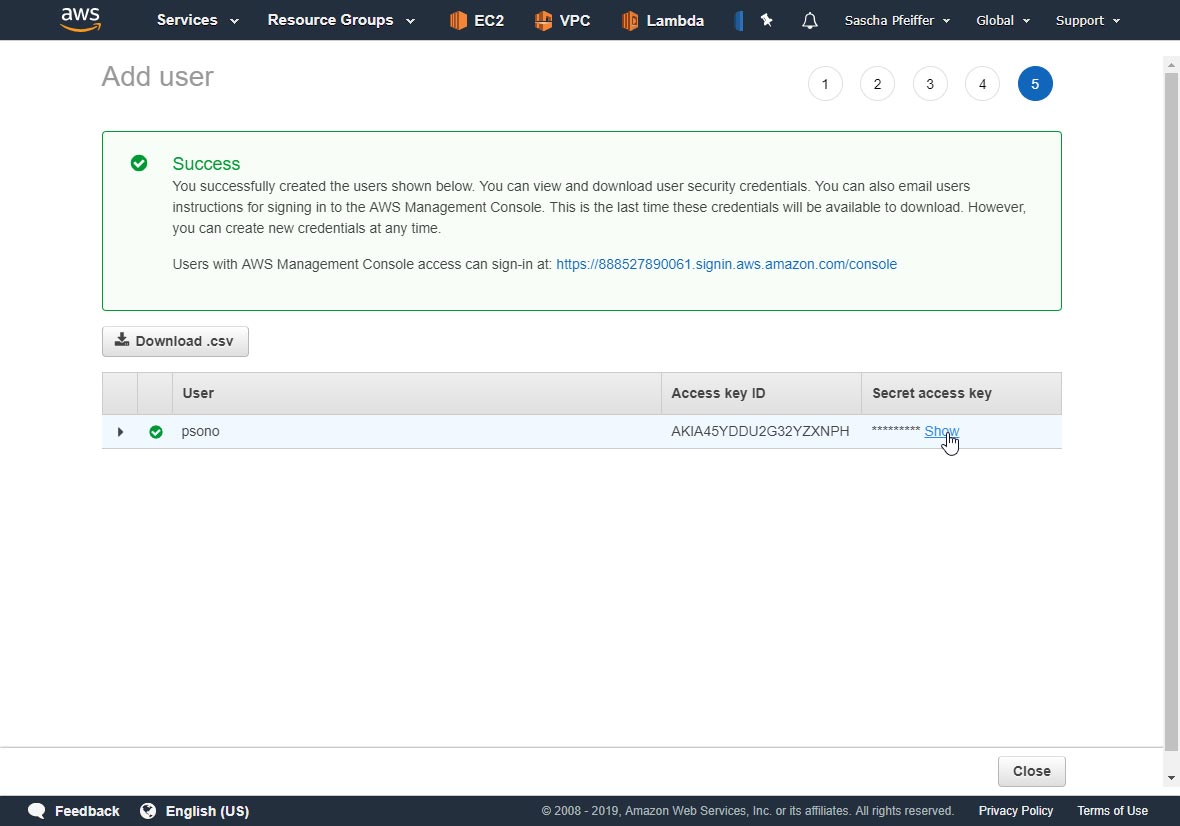
Acquire "Access key ID" and "Secret access key"
# Configure Logging
Configure Psono server
There are a couple of variables that you need / can adjust in the
settings.yamlS3_LOGGING_BUCKETThe bucket nameS3_LOGGING_ACCESS_KEY_IDThe access key IDS3_LOGGING_SECRET_ACCESS_KEYThe secret access keyS3_LOGGING_SECRET_ACCESS_KEYThe secret access keyS3_LOGGING_PREFIX(optional) May be used to prefix the log file and potentially a subfolder (e.g.psono-audit-logs/)
TIP
Don't forget to restart the server afterward.
